Network Sniffing on a Budget: Malware Detection with Suricata

Most people think intrusion detection needs powerful servers and commercial software. But Suricata runs fine on low-end x86 boxes, especially if you keep it passive. This project outlines how I used a spare thin client with Alpine Linux to sniff mirrored traffic from my firewall and catch signs of malware using Emerging Threats.
Hardware & Network Setup
The system is an old fanless mini-PC with 2 Intel NICs and 2 GB RAM. I installed Alpine Linux (persistent disk install), assigned one NIC as a management interface, and the other as a dedicated sniffing interface connected to a mirror port (SPAN) on my router.
The firewall/router mirrors all LAN+WAN traffic to this second NIC, letting Suricata see everything without interfering.
This setup also works in a virtual machine with two NICs, one configured by DHCP, and one left “just up” for passive monitoring or PCAP replays.
Installing Suricata on Alpine
Suricata is available directly from Alpine’s community repository:
apk add suricata suricata-openrc
This installs the engine, configuration in /etc/suricata/, rule files under /var/lib/suricata/rules/, and service support via OpenRC.
Fetching Rules
Download the Emerging Threats open ruleset without overwriting the defaults:
curl -o /var/lib/suricata/rules/emerging-all.rules https://rules.emergingthreats.net/open/suricata/emerging-all.rules
Then, edit /etc/suricata/suricata.yaml and modify the rule list:
rule-files:
- suricata.rules
- emerging-all.rules
This extends the detection surface with thousands of community-contributed signatures for malware, botnets, suspicious DNS, phishing, and more.
Configuring Suricata
Make sure the sniffing interface (e.g. eth1) is up but not configured:
ip link set eth1 up
In /etc/suricata/suricata.yaml, configure af-packet for passive packet capture:
af-packet:
- interface: eth1
cluster-id: 99
cluster-type: cluster_flow
defrag: yes
Limit Suricata’s outputs to what you actually want to inspect:
outputs:
- eve-log:
enabled: yes
filetype: regular
filename: /var/log/suricata/eve.json
types:
- alert:
metadata: yes
- http
- fast:
enabled: yes
filename: /var/log/suricata/fast.log
Starting the Service
Enable and start Suricata:
rc-update add suricata
rc-service suricata start
If everything is set correctly, it will begin passively processing traffic on eth1.
Testing Alerting (SID 2100498)
A quick way to confirm that Suricata is working is to trigger rule SID 2100498 from the Emerging Threats ruleset. It alerts on any response containing uid=0(root).
Start watching the alerts:
tail -f /var/log/suricata/fast.log
Then, from any browser or terminal on your LAN:
curl http://testmynids.org/uid/index.html
You should see output like:
[1:2100498:7] GPL ATTACK_RESPONSE id check returned root [**] [Classification: Potentially Bad Traffic] [Priority: 2] {TCP} 18.245.175.66:80 -> 192.168.x.x:54918
Or the JSON form in /var/log/suricata/eve.json:
"signature": "GPL ATTACK_RESPONSE id check returned root",
"category": "Potentially Bad Traffic",
"severity": 2
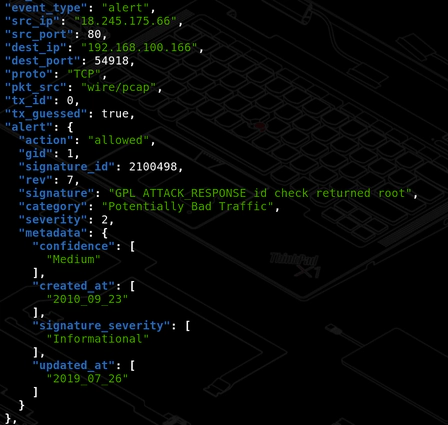
This confirms Suricata is capturing mirrored traffic and detecting threats using the provided rule set.
Monitoring Real Traffic
Once deployed, Suricata writes alerts to /var/log/suricata/eve.json and /var/log/suricata/fast.log. To inspect live alerts:
tail -f /var/log/suricata/eve.json | jq 'select(.event_type == "alert")'
You’ll see entries like:
ET MALWAREET CNCET POLICYET TROJAN
These cover known exploit kits, malware callbacks, tunneling, DNS abuse, and other threats.
Final Thoughts
Suricata turns a cheap Alpine box into a passive intrusion detection system that’s dead silent and effective. Combined with a mirror port and strong ruleset, it gives you visibility into your network without needing to be inline or disruptive.
In my case, this setup flagged:
- An IoT camera connecting to random IPs in foreign ASNs
- A Windows PC hitting typo-squatted domains
- Misconfigured smart devices leaking traffic over HTTP
Tip
Want to deploy this yourself? Check your router or switch config for SPAN/mirror port support. Many consumer devices (OpenWRT, MikroTik, EdgeOS) support traffic mirroring to a secondary NIC.