Reversing, Rebuilding, and Failing Better: My Cyber Security Challenge Belgium Qualifier Experience

On March 14 and 15, I joined the Cyber Security Challenge Belgium qualifiers with three teammates. For two days, we threw ourselves at CTF challenges covering binary exploitation, Android reversing, cryptography, and more.
What follows is a recap of the challenges I personally worked on, some I solved, some I didn’t, but all of them left me with new skills and new ideas.
A Buffer Overflow to Warm Up
One of the first challenges I picked involved a binary with a basic stack overflow. I used standard techniques, finding the offset, hijacking the return address, and injecting shellcode. Tools like pwntools helped automate the payload crafting. It was a great warm-up and a confidence boost once it worked.
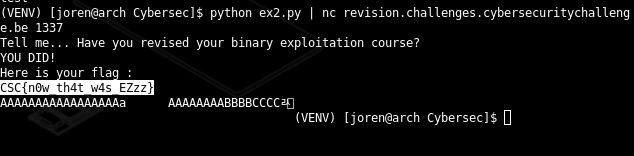
OurEncIsSec: Zip Bombs and OEIS
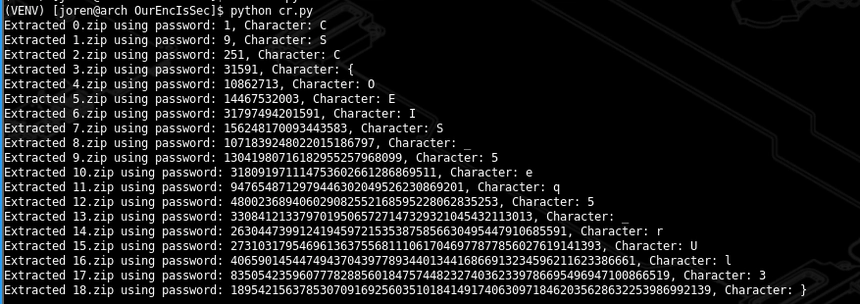
Then there was a more elaborate cryptography challenge: 18 zip files, each password-protected. We cracked the first three passwords using John the Ripper and got numeric values from them. I searched the sequence in OEIS and found it matched A007408, which gave us the full pattern of passwords.
Using this, I could extract all zip contents automatically, reconstruct the password-protected message, and finally reveal the flag.
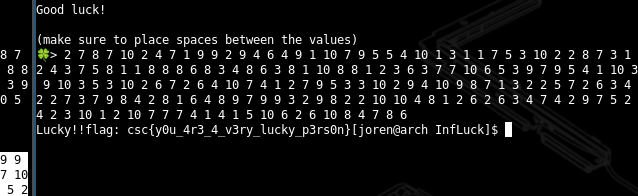
Infinite Luck: One in a Million?
One challenge involved “guessing” a thousand random numbers between 1 and 10. The banner claimed it required infinite luck, but of course, the randomness was seeded. After inspecting the generator, I realized it was deterministic. By precomputing seeds and output sequences, I could match the challenge’s banner to a specific seed and regenerate the entire solution.


Android Reversing: FRIDA and JADX
Several APKs were part of the qualifier set. I used JADX to decompile them and FRIDA to patch logic at runtime. In one challenge, I bypassed license validation by forcing key methods to return true and unlocking hidden functionality.
The Challenge That Stuck with Me: Rebuilding a Split DEX
This one stood out.
The app used a 4×8 button grid. Pressing buttons loaded a sequence of blockXX files from assets. These were concatenated in-memory and passed into InMemoryDexClassLoader to load a class called be.dauntless.flag.Flag.
Class loadClass = new InMemoryDexClassLoader(ByteBuffer.wrap(byteArrayOutputStream.toByteArray()), getClassLoader())
.loadClass("be.dauntless.flag.Flag");
Each block was a fragment of a DEX file, but the app didn’t tell you the right order. I tried manually inspecting the fragments, identifying methods, string constants, and offsets, to infer how to reassemble the full file. I got close, but didn’t crack it in time.
That challenge stuck with me because it combined static analysis, runtime introspection, and logic reconstruction. It wasn’t just technical, it was creative.
The One That Got Away: TLS Fingerprinting
Another challenge involved a Go-based TLS server that rejected all client connections unless they matched a specific fingerprint. I used Go’s tls.Config to replicate the version, cipher suites, and ALPN:
tls.Config{
MinVersion: tls.VersionTLS13,
CipherSuites: []uint16{
tls.TLS_AES_128_GCM_SHA256,
// ...
},
NextProtos: []string{"h2"},
}
Despite that, the server still refused the connection. I suspect it was using JA4 or similar TLS fingerprinting techniques we couldn’t fully emulate. We had to move on, but I’d love to revisit that one someday.
Final Thoughts
I didn’t solve everything. But that wasn’t the point. Every challenge was a practical puzzle, something to decode, reverse, bypass, or just understand a little better.
Working as a team with Evarist, Nathan, and Waut made it even more valuable. We bounced ideas off each other, divided tasks, and got a much broader set of challenges covered.
The Cyber Security Challenge Belgium qualifiers weren’t easy. But they were the best kind of difficult, the kind that teaches you something whether you solve the problem or not.